Centralized Digital Currency
Now, we can come up with an assumption, we use the digital currencies issued by the central bank. Each digital currency is signed by the central bank’s private key, everyone can prove whether the currency they received is true because the public key corresponding to the private key is publicly available. Even though the system doesn’t seem to have any problems, the biggest problem is that the digital currency system doesn’t use the block chain. If a man receives a digital currency that values at one hundred dollars, he can purchase goods of equal value in the supermarket by paying the currency. Everything seems to be perfect. But the nature of digital currency is a file, the man can copy the file infinitely, so the man will have countless amounts of money. That’s terrible, the situation, known as the double spending attack, will cause the system to be broken.
The previous digital currency system is terrible, but now we make some improvements to the system. The central bank sends digital currencies to people and stores the ownership of every digital currency in its database. When a person wants to use digital currency to pay for something, the sender will check the ownership of the digital currency. If the ownership isn’t consistent with the sender, the payment will be a failure. Similarly, if the check is successful, the central bank must change the ownership of the digital currency in its database.
Decentralized Digital Currency
A decentralized digital currency system must solve the following two problems. One problem is the power of issuing digital currency, who can issue digital currency, the amount of digital currency to be issued, and when it can be issued. The other is how to prove the validity of transactions, and how to defend against the double spending attack. We can establish a data structure maintained with all users, known as the block chain.
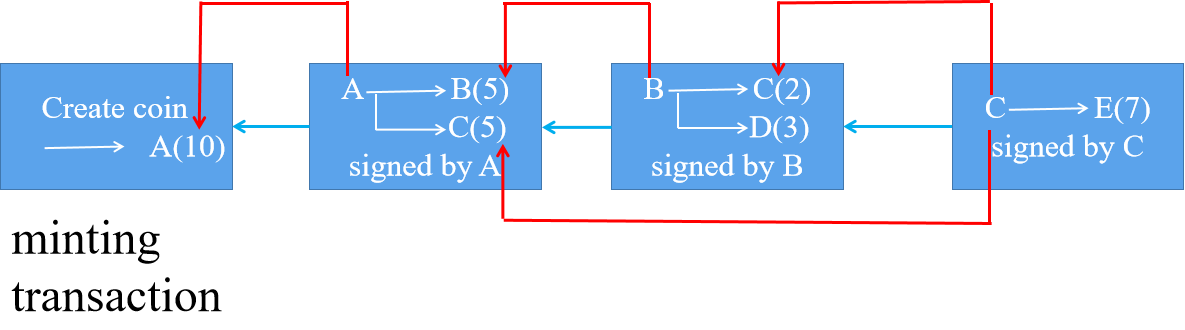
As shown in the following diagram, a user called A gains the ownership of issuing digital currency called the power of minting, and A will receive ten Bitcoins. The transaction is called a minting transaction. After A has received ten Bitcoins, A send five Bitcoins to B and C respectively. The transaction is signed by A and also states where the ten Bitcoins come from. Each transaction in the Bitcoin system contains two sections. One is the input section, which states where the Bitcoins will be sent come from and some other messages. And the other is the output section, which states the receiver’s public key. When B receives the Bitcoins, it sends two Bitcoins to C and three Bitcoins to D. Similarly, the transaction is signed by B and states where the Bitcoins sent come from and where to be sent. Until now, C has seven Bitcoins, and it decides to send them to E. When E receives the Bitcoins, five of seven are from the second transaction and two of seven are from the third transaction.
How does a user initiate a transaction? The user must know the public key of the receiver. The transaction describes where the Bitcoins will be sent come from, the public key of the receiver, and the public key of the sender. Why the transaction contains the sender’s public key? It is used to broadcast the transaction launcher. But are there any risks? If an attacker launches a transaction signed by itself and states another’s public key. When other nodes receive the transaction, they will prove the transaction by using the attacker’s public key, the result will be correct of course. Therefore, will others’ Bitcoins can be stolen? The answer is not. Because the input section of the transaction describes where the Bitcoins come from. The validator nodes will find a transaction according to the public key stated in the current transaction, which states where the Bitcoins were sent to, and the receiver in the transaction is not consistent with the sender of the current transaction, so the check will fail and the transaction will be refused.
Block header and block body
block header
- version
- the hash pointer of the previous block header
- the Merkle tree root hash
- target
- nonce
block body
- transaction list
Consensus in Bitcoin
simple poll
This mechanism is the membership, which nodes can join to maintain the block chain. The poll mechanism is valid for the affiliate chains because all nodes are defaulted to have no malicious. If the Bitcoin system adopts the mechanism, once there is a malicious super node in the system, it may generate a lot of accounts. When the accounts generated by the malicious node occupy more than fifty percent, the node will have the control power of the system and it can manipulate the result of voting. This kind of attack is known as the Sybil attack.
POW
Only the node that has the bookkeeping rights can package transactions and issue the next block. The process to gain bookkeeping rights is called mining. The mining is to find a random nonce contained in the block header, which has four bytes. When Hash(block header) is less than or equal to the target and all the transactions are valid, the node can package the transactions list, issue the next block and it will get a reward. Thus, the process is used for proof of work and is also called POW. However, if we know the nonce, everyone can prove it easily by calculating hash value—— Hash(block header). This characteristic is also known to be difficult to solve, but easy to verify.
forking attack
Bitcoin system requests all nodes to maintain the longest valid chain. An attacker could insert a block before the current block, which will cause the fork to occur and one block chain to change to two block chains. This kind of attack is called the forking attack.
In addition, two miners might get bookkeeping rights meanwhile, one is called miner A and the other is called miner B. The two miners both package some transactions and issued the next block to the Bitcoin system. Because of the network delay, different miners might update the block chain with the different blocks, some miners may receive the block issued by miner A firstly while others may receive the block issued by miner B firstly. Therefore, the system has two block chains temporarily whose length is equal. The situation is called the temporary fork. The situation will maintain a period until one of the chains is longer than the other.
Reference
- Bitcoin and Cryptocurrency Technologies A Comprehensive Introduction [Arvind Narayanan, Joseph Bonneau, Edward Felten, Andrew Miller, Steven Goldfeder]
- http://zhenxiao.com/blockchain/
文档信息
- 本文作者:wendaocsmaster
- 本文链接:https://wendaocsmaster.github.io/2023/02/17/block-chain-Bitcoin-protocol/
- 版权声明:自由转载-非商用-非衍生-保持署名(创意共享3.0许可证)